We recently highlighted that the health sector appeared to be the most vulnerable to data breaches. On 30 October 2018, the Office of the Australian Information Commissioner (OAIC) released statistics on data breaches notified to the OAIC during the September quarter.
According to the OAIC, it received 245 notifications of data breaches under the notifiable data breach (NDB) scheme between 1 July-30 September 2018. Based on the submitted reports, 57% of the data breaches were attributed to malicious or criminal attacks (compared to 59% in the previous quarter), while 37% of the breaches were attributed to human error (compared to 36% in the previous quarter).
The majority of notified breaches affected 100 or fewer individuals (63% of notified breaches), with data breaches affecting between 1-10 individuals comprising 41% of the breaches notified to the OAIC.
The latest quarterly report continues to highlight that organisations should proactively manage data privacy and cyber security in order to minimise the risk of a NDB occurring. These steps include:
- regularly undertaking privacy audits to destroy or de-identify personal information that is no longer required;
- updating the organisation’s information handling processes, procedures and systems (including the privacy policy and collection statements) to ensure that they are consistent with the organisation’s legal obligations;
- embedding a culture of respect for privacy among staff through regular training on privacy and cyber security; and
- developing, implementing and testing a data breach response plan and an information privacy strategy that is endorsed by the organisation’s board.
Figure 1: Notifications per month - Source: Office of the Australian Information Commissioner
Steps to take
|
|
Reduce the likelihood of breach
|
Organisations must take reasonable steps to destroy or de-identify personal information if the information is no longer required for the purpose(s) for which the information was collected and there are no legal requirements to keep the information. Lawfully reducing the quantity of information held by an organisation is a good start to reducing exposure to a data breach. |
Update information-handling processes
|
Ensure that the information handling processes, procedures and systems are consistent with the organisation’s legal obligations. This involves implementing technological measures (e.g., anti-virus and firewall software and security updates and releases), as well as requiring employees to regularly change their passwords. Consider implementing two-factor authorisation to restrict access to particularly sensitive information. Review and update privacy policy and collection statements to reflect current practices regarding collection, use and disclosure of information. |
Embed a culture of respect for privacy
|
A key contributor to NDBs is employee error, so developing and embedding a culture internally of cyber resilience and privacy compliance is essential to minimising the risk of a NDB occurring. Staff training should focus on how a data breach might occur, what employees should do if they see or suspect a data breach and how the organisation will respond to a data breach. |
Create and implement a strategy
|
Underpinning an organisational approach to the issue should be an information privacy and cyber resilience strategy (endorsed by the board) which incorporates a data breach response plan. The strategy should inform how an organisation will maintain cyber resilience and empower the organisation's senior management to minimise the risk of a NDB. The data breach response plan should outline how the organisation will promptly respond to a reported data breach, including information on who will manage the response to the NDB. It is important to regularly review and update the strategy and plan to account for evolution in the organisation's business and technology. |
Number of reported NBDs (all sectors)
The OAIC reported that at least 76 NDBs were reported per month in the September 2018 quarter (down from a peak of 90 NDBs reported in June 2018):
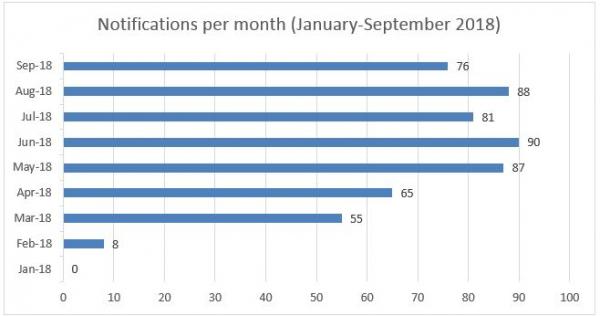
Figure 1: Notifications per month - Source: Office of the Australian Information Commissioner
The majority of NDBs affected 100 or less individuals (63% of NDBs reported during the quarter). Data breaches affecting between 100-1,000 individuals comprised 27% of the NDBs reported to the OAIC, while NDBs affecting between 6% of reported NDBs. Five NDBs were notified to the OAIC affecting between 5,000-250,000 individuals, while four NDBs were reported where the number of affected individuals was unknown at the time of notification.
Kinds of information affected
Based on the information reported, the OAIC noted that many NDBs affected multiple types of information at the one time. According to the OAIC:
Table 1: Kinds of information affected – source: Office of the Australian Information Commissioner
Information type
|
Current quarter
|
Previous quarter
|
QonQ change
|
| Contact information |
85% |
89% |
-4% |
| Financial details |
45% |
42% |
+3% |
| Identity information |
35% |
39% |
-4% |
| Tax file number information |
22% |
19% |
+3% |
| Health information |
22% |
25% |
-3% |
| Other sensitive information |
7% |
8% |
-1% |
Source of breaches (all sectors)
Based on the information reported to the OAIC, the OAIC determined that 57% of the NDBs reported during the quarter were caused by malicious or criminal attacks, compared to human error accounting for 37% of the NDBs and 'system fault' accounting for the remaining 6% of reported NDBs.
The OAIC noted that 'malicious or criminal attacks' are 'deliberately crafted to exploit known vulnerabilities for financial or other gain'. Such attacks include phishing attempts, malware, ransomware, brute force attack and hacking by other means (collectively, 96 NDBs reported to the OAIC during the quarter was as a result of such 'cyber incidents'), social engineering or impersonation (responsible for 12 NDBs reported during the quarter) and actions taken by a rogue employee or insider threat (responsible for 14 NDBs reported during the quarter). Paperwork or storage devices being stolen is also counted as a malicious or criminal attack by the OAIC (17 NDBs reported during the quarter).
The OAIC drilled down further into the types of human error responsible for NDBs reported during the quarter:
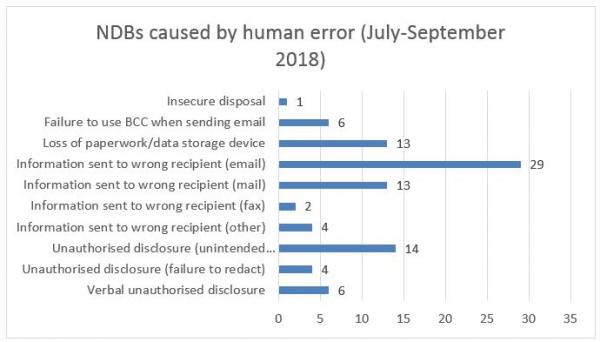
Figure 2: NDBs caused by human error (July-Sept 2018) - source: Office of the Australian Information Commissioner
For further information, please contact Michael Gorton AM or Andrew Chalet.
If you'd like to stay up to date with more Russell Kennedy insights, please sign up here.